T
hese days there aren’t enough ways to protect your privacy on the Internet. You can choose from a great deal of software solutions to do this but, as always, the free ones might prove to be the best. So, let’s see what you can do to be as stealth as possible during the hours (days?) of staying online.
How you can stay anonymous on the web
The first thing you might think of is a proxy. Yes, this might be a pretty good solution if it is an anonymous proxy that you can rely on but, in the long run, and if you have enough experience on the web, you will understand that you can be easily traced because of the direct connection that you will have with the proxy.
In case you didn’t already know, most of these proxies, although being out there for public use, do make logs of all connections, and this is bad news for anonymity. Also, hackers can have their own public proxies that will allow them to log everything you do online and easily steal even the most sensitive information from you without you even knowing it. How? Simply by going through the logs of unencrypted data you have sent to the web through the proxy server using a direct connection. Therefore, the proxy solution is out.
There are also websites that guarantee you an anonymous browsing experience but most of them will add their own frames containing advertising to the websites you visit. Another reason for not using such a solution is that a lot of the scripts on the web pages you will open in your web browser will completely refuse to work.
That happens because said websites do not accept all types of scripts to run through the proxies they are using to provide you with anonymity. And, again, the logs come up for discussion. If you do believe that your privacy is the most important thing to you or you simply have something to hide, such websites are not the answer.
You can also go for the paid services that can get you browsing anonymously on the web in an instant. All you have to do is install the software they send you and the software takes care of everything for you (after you set up your browser, instant messenger or whatever other app you want to be stealth to use the paid anonymous service).
Such solutions will allow you to use encrypted connections to their servers, which will then connect to the web and retrieve the information you want for you, sending it back in the same encrypted form. Sounds very good and indeed it is quite a nice thing to go for if you’re in need of online privacy. If you are ready to go for the paid approach, such solutions might be Hotspot Shield or WebGhost, but why not go for the free ones?
The things you should go for
What are the free options you ask? Well, as most people who have used them agree, they are probably better than the paid ones and you will see immediately why that is.
The two online free anonymity providing solutions that just stand out from the crowd are Tor and JAP. While Tor is widely used and known, JAP might just be a new one for you, although, despite its lack of popularity as compared to the former, during our tests it has delivered on all it had promised. In fact I’m using it right now while writing this article and, despite a small delay after hitting enter, everything is loading in my browser as smoothly as possible (truth be said, the connection speed may vary but it has never failed me while using it – actually I’m quite impressed, to say the least, because at the moment I totally forgot I was using JAP at all).
What Tor is and how it works
Let’s start with Tor. I would want to personally let you in on what Tor does to protect your privacy and how it does it, but this has already been covered by the Tor Team on their website and so I will let them explain what it is all about: "Tor is a software project that helps you defend against traffic analysis, a form of network surveillance that threatens personal freedom and privacy, confidential business activities and relationships, and state security. Tor protects you by bouncing your communications around a distributed network of relays run by volunteers all around the world: it prevents somebody watching your Internet connection from learning what sites you visit, and it prevents the sites you visit from learning your physical location. Tor works with many of your existing applications, including web browsers, instant messaging clients, remote login, and other applications based on the TCP protocol."
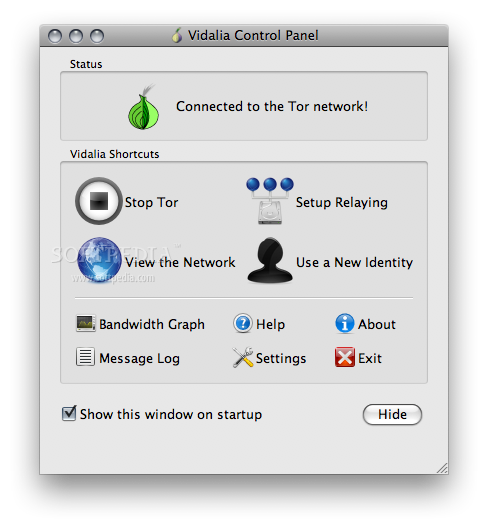
Vidalia's Control Panel, the GUI that helps the user manage Tor
Enlarge picture
What this means is that Tor actually uses an anonymous, distributed network of relays through which your traffic will be redirected and encrypted using random virtual tunnels so that no one, not even the ones that run those relays, will know what data you send and from where or to where your data travels on the Internet.
The fact that each network node is able to see no more than one single hop of all of your paths to the end point of the circuit means that those who would want to capture and analyze the data you are sending and receiving to and from the Internet will miserably fail in their attempts. And this brings us to the point. Top notch privacy on the web for free!
The only thing that you might want to be careful with while using Tor to make your browsing experience as secure as possible is make sure that you set your browser not to exchange cookies with the websites you visit and remember not to give out any information concerning your identity.
The inner works of JAP
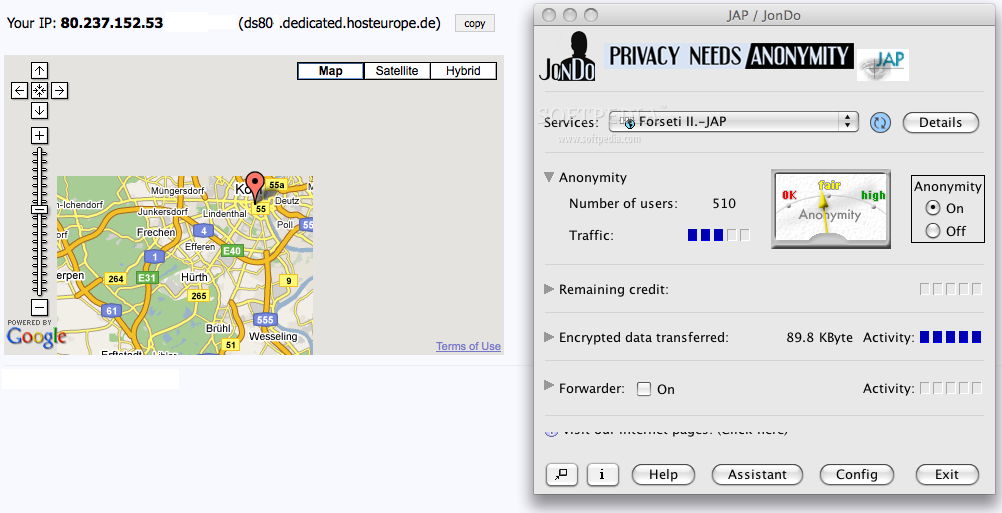
JAP on the other hand, does not rely as much on the random factor as Tor but still manages to come on top of the class. It will help you take a little detour from the conventional way to the server hosting the website you want to visit by telling your browser to connect through a network of several intermediary servers aka Mixes, which form a sequence named Mix Cascade. These types of server arrays through which you can connect to the web are predetermined and you can choose from a bunch of them using the JAP interface.

JAP's interface that will help you choose one of the mix cascades and the proof that it works
The smart thing lies in the fact that if the number of users using a certain mix cascade is larger, the anonymity level provided by it is higher. Why? Because the connections created by the users between the mixes will mingle and no one will ever be able to understand a thing through all that mumbo jumbo going around there. This means that users are completely safe because it is impossible to determine which connection belongs to which user.
If you are worried about the mix providers, here’s a hint: you shouldn’t be. Why? Because each of these mixes are provided by institutions that will be asked to officially declare that they will not exchange the data they can log on their servers with other mix providers from the network or even keep log files at all.
The Network settings in Firefox
Enlarge picture
And, now, the best part of all this: all information about these providers is made public and verified by the JAP Team and, based on this information, users will be able to choose the mix cascade they trust the most.
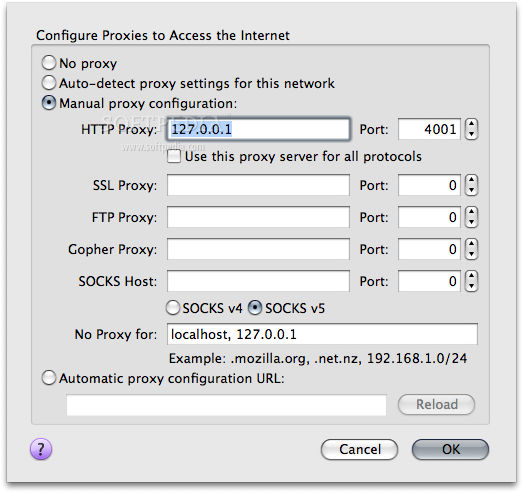
Both Tor and JAP can be downloaded from Softpedia and their installation is pretty much self-explanatory. To configure them so that they will work with your favorite browser you will just have to open the Preferences window, go to the Network Settings and enter 127.0.0.1 as the proxy IP address and 8118 as the port for Tor or 4001 for JAP.
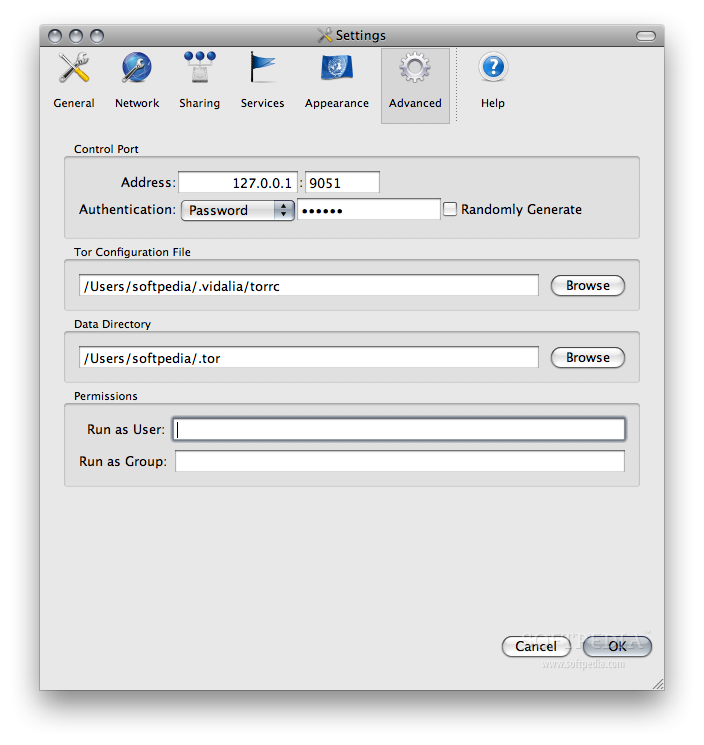
Tor will, however, allow you to further customize the settings for your proxy by going to the Advanced tab in the Settings window that you can open from its Control Panel. On the Advanced tab you can manage the password to be used for authenticating to the Tor network, select a custom configuration file or the data directory and even set the run permissions.
The Advanced tab on Vidalia's Preferences window
In case you manage to lose yourself in the sea of Nexts when installing and/or configuring Tor or JAP, these are the how-tos on installing and configuring them on your Mac: HERE for Tor and HERE for JAP.
One last reminder: you have to remember that there are no perfect anonymity solutions out there. The best thing to do if you really care about your privacy is to be careful which websites you exchange information with and pay attention to what type of information you disclose about yourself when online.
Do you know of other anonymity protection solutions that we missed? Do you know of other ways one can protect one’s privacy online? Then leave us a word in the comments.
Best regards,plzz comment if u like it